Here’s how North Korean hackers are still getting paid in crypto despite sanctions
TRM Labs says North Korean IT workers have laundered millions in USDC and USDT while secretly working for blockchain startups.
North Korea continues to rely on crypto to quietly fund its weapons programs and the U.S. government is stepping up efforts to shut it down. On July 8, the U.S. Treasury’s Office of Foreign Assets Control sanctioned a North Korean hacker, Song Kum Hyok, who they say helped organize a widespread scheme involving fake remote workers at unsuspecting tech and crypto companies.
According to a recent report from blockchain forensic firm TRM Labs, Song was linked to Andariel, a cybercrime unit that’s part of North Korea’s military intelligence. They explained that he played a key role in placing IT workers — most of whom were actually North Korean operatives — into jobs at U.S. companies by using stolen American identities and fake documents.
Many of these jobs were in web3, crypto infrastructure, or blockchain-related software development.
TRM Labs said these workers operated from countries like China and Russia while pretending to be U.S.-based freelancers. They got paid in stablecoins such as USD Coin (USDC) and Tether (USDT). From there, the money appeared to have flowed through layers of wallets, mixers, and conversion services before ending up in the hands of the North Korean regime.
Analysts at TRM Labs pointed out that this is just the latest sign that North Korea’s Reconnaissance General Bureau — the same agency behind Lazarus and Bluenoroff — is still using cyber tactics to support military goals. Treasury officials, they noted, have been warning that crypto theft and identity fraud remain central to North Korea’s strategy for avoiding economic pressure.
The analysts explained that the scheme uncovered by OFAC relies heavily on fake personas. Song was allegedly responsible for building those fake identities, using stolen data from real U.S. citizens. Once hired, North Korean operatives may have worked for months or even years in U.S. companies under false names.
They also noted that OFAC sanctioned four companies and one other person connected to a Russia-based network that allegedly helped manage these fake IT jobs. These businesses reportedly signed long-term contracts with DPRK-linked firms and were aware they were dealing with North Korean workers.
Many of the workers targeted jobs in the crypto sector specifically, where payments were easier to anonymize. Once the crypto was received, TRM Labs analysts said, it was spread across several wallets and eventually converted into fiat using OTC brokers, some of whom have been previously sanctioned.
Cyber alliance
The latest OFAC’s action followed a series of coordinated moves by U.S. agencies, including the Department of Justice and the FBI. On June 5, 2025, the DOJ also filed a civil forfeiture complaint seeking to seize over $7.7 million in crypto, NFTs, and other digital assets believed to be linked to the same North Korean network.
TRM Labs says the workers used identities like “Joshua Palmer” and “Alex Hong” to get hired at crypto startups and other tech firms. They were paid in stablecoins, with proceeds routed through centralized exchanges, self-hosted wallets, and then on to higher-level regime figures like Kim Sang Man and Sim Hyon Sop, both already under U.S. sanctions.
The DOJ’s investigation, according to analysts, revealed that parts of the operation relied on infrastructure based in Russia and the UAE. Investigators found the use of local IP addresses and forged documentation, which helped the North Korean workers hide their true identities. This, they said, underscored just how international the scheme had become.
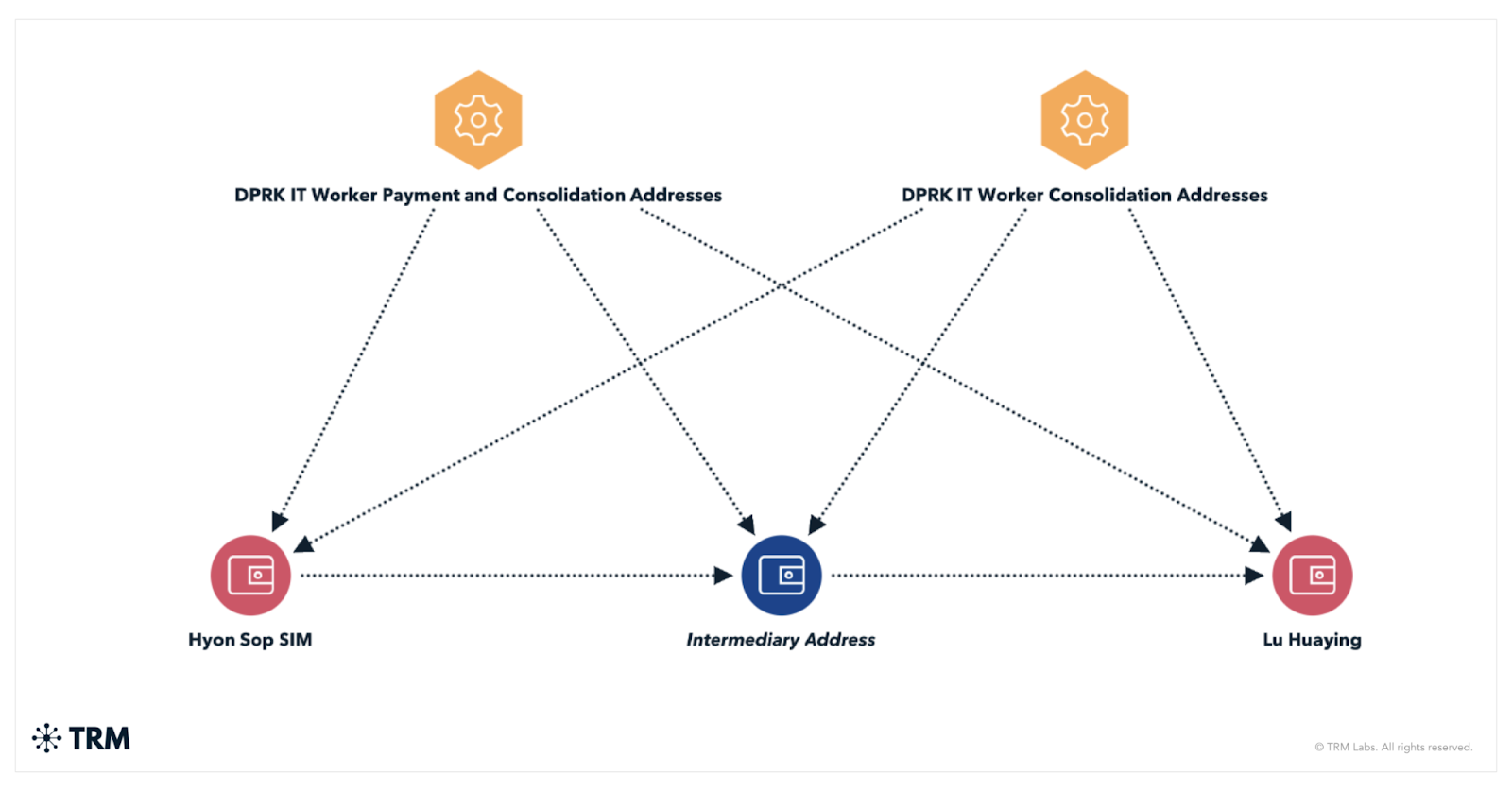
Blockchain data reviewed by TRM showed that once funds reached mid-level wallets, the money was split into smaller portions, routed through privacy-enhancing tools, and eventually exchanged for fiat via OTC desks. One of those OTC brokers had already been sanctioned by OFAC in late 2024.
As for law enforcement efforts, the FBI and other agencies successfully seized a portion of the laundered digital assets, including USDC, ETH, and some high-value NFTs. The analysts described these seizures as part of a broader laundering strategy meant to break up the money trail and make detection far more difficult.
TRM Labs says the U.S. government’s latest action sends a message that crypto remains a high-risk channel for sanctions evasion, especially when it comes to North Korean operations. The blockchain intel firm warned that companies hiring remote developers — especially in the blockchain space — need to take extra care in verifying who they’re really dealing with.
You May Also Like

Securities Fraud Investigation Into Corcept Therapeutics Incorporated (CORT) Announced – Shareholders Who Lost Money Urged To Contact Glancy Prongay Wolke & Rotter LLP, a Leading Securities Fraud Law Firm

Microsoft Corp. $MSFT blue box area offers a buying opportunity
